
Cyber: The Twitter Hack of 2020
On the 15th July 2020, twitter was subject to hack where someone was able to break into accounts, reset their password, steal their data and even tweet. In total, 130 accounts were targeted but only 45 of these appear to have been successful as all these accounts tweeted about a bitcoin scam.
The scam was simple, users were told that the account holder would "give back to the community" by accepting bitcoin payments to an account and all payments would be doubled and sent back, free of charge. So, if you sent £1,000 worth of bitcoin to this address, you'd be sent back £2,000. The trick was that the tweet stated this would only last 30 minutes or that they'd only offer $1,000,000 worth of trade backs. While this doesn't sound completely believable, in a bad moment where you'd not quite thinking straight you might be tempted and the issuing of a time or stock limit may make you more susceptible to a quick purchase.
Something else that helped with this scam was who was hacked and tweeted this. Notable figures such as Elon Musk who has been known for his "strange" tweets at times, Jeff Bezos who has more than enough money, Kanye West who's known for supporting his community and many more. I've listed a few notable ones below but for a full updating list, please see this link.
- Apple
- Mike Bloomberg
- Barack Obama
- Bill Gates
- Binance
- Coinbase
- Uber
- Cashapp
So that's what happened, but a better question is how did this happen, recent speculation has shown some people thinking admins had access to tweet onto anyone's account or view DMs but this isn't true for the most part. The actual attack was mainly orchestrated via one user online found within an online group called OGUsers.com. This is a site where usernames for different accounts are traded with names that are 1-2 digits in length such as @y on twitter. This user went by the name 'Kirk'. Kirk allegedly gained access to login credentials to an inside twitter tool via an internal slack channel where the login credentials had been posted. For more information into who these people are and who made the media aware to Kirk, you can check out this article by The Verge which explains more about who these anonymous people were who helped break the story. How he got access to this view is unknown, but some speculate by paying off an employee or via some form of social engineering which I'll cover in a later post. Once Kirk had these credentials, he was able to log into an account which had some administrative power or allowed for an existing account to gain this power and was able to get an admin view over twitter.
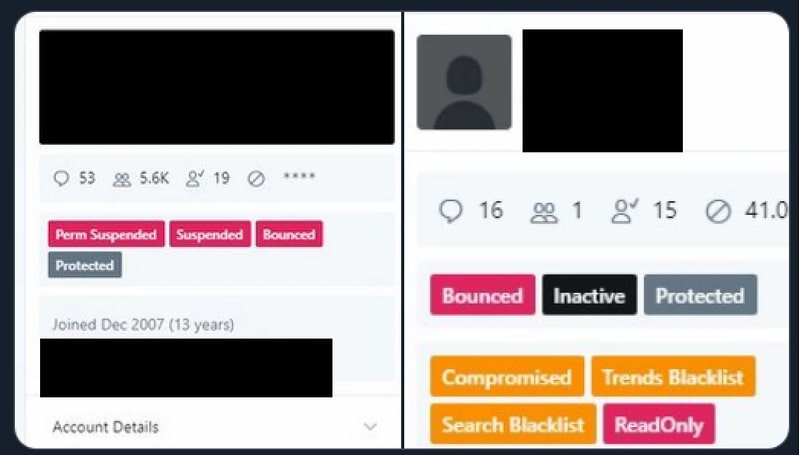
Kirk then had access to this panel. This gave him a basic view of the accounts however, not complete access by default. From this administrative view, we can see that he was able to find details about the account such as number of followers, tweets and other features, what the account's current state was such as suspended, inactive, protected and more. It's a little confusing as certain elements have been redacted by the publisher of this image because Twitter is now reporting spreading uncensored versions of this image on Twitter, so this was the only version I've found so far. But, looking at the bottom left we can see when this user joined, pacifically Dec 2007 and below that is a dropdown of the account details. This would lead us to belief that Kirk was able to view private information about these accounts that isn't publically accessible such as the email address associated with the account, a possible phone number if they have enabled 2-step authentication, full name and address and even more. We can't be certain as this is only speculation, but Twitter does keep more information about your account that is required to create the account but isn't publicly shared. But this view doesn't directly show a method for Kirk to tweet from any account like we saw.
It's believed he then changed the associated email address with the targeted accounts and was then able to send a password reset to these emails, allowing him to login and tweet. At this point he was theoretically able to gain complete control of the account as he now controlled the email associated with the account and had the new login credentials. That's when he then started the bitcoin scam and took twitter by storm. Why he stopped after compromising 45 accounts we're unsure, however it's likely that once Twitter figured out it was an issue with an administrative account that they looked at which account was being accessed and were able to shut it down.
The thing about this attack is that in total, Kirk made off with $118,482.65, of which $42,000 was from a single transaction, related to a Japanese stockbroker. However, this is next to nothing in terms of both money and power. This is a relatively small amount when it comes to bitcoin itself but the real issue comes to what was done when Kirk had access to these accounts. He was able to compromise the accounts of some of the biggest people on twitter and force them to stop verified accounts from tweeting all together. The impact this hack could have had is incredible to think, if he'd tweeting something profound from Biden's account it may have cost him a chance at the presidency, or if he'd manipulated Elon Musk's account to tweet something relating to Tesla this may have caused the stock price to drastically drop.
The takeaway here is that while this attack was extremely powerful and had the makings of a very bad situation, Twitter got very, very lucky.
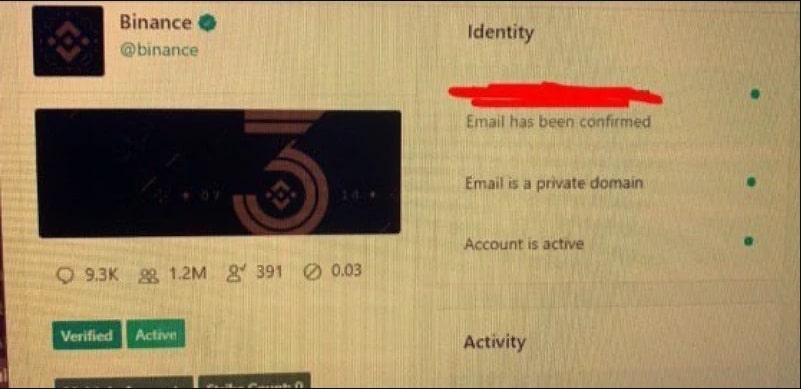
Above is an one of the accounts Kirk was able to gain access to, Binance. Binance are a bitcoin exchange company that deal with a variety of different coins such as Bitcoin, ethereum, Ripple and many more. The fact Kirk was able to gain access to accounts which directly related to Bitcoin was one of the reasons why the attack was as effective as it was, the fact an actual crypto currency exchange publicly announced this helped Kirk's story immensely. However, one thing that hasn't been talked about yet is the fact that Kirk was able to download some of data from Twitter. On 8 of the 45 accounts that were hacked, Twitter's option to download all of your data relating to twitter was executed on these accounts, their identities unknown. None of the 8 accounts were verified, but it did mean that Kirk got everything related to their accounts from all personal information, list of followers/following, all their recent DMs, everything they've liked or retweeted, everything. We're unsure to why it was only the non-verified accounts that had their data stolen, but we can presume it may be related to their verified status.
Now could something like this attack ever happen again? It's hard to say. While they may improve the backend to prevent employees from being able to change associated emails or what level of access they get, it's never certain as new bugs appear with every update and some are yet to be found. Their is also always the risk of someone like Kirk, manipulating another Twitter employee, getting their credentials and causing more mess via a different tactic, or just selling off these credentials to some nation state to begin an extremely large scale attack that would be unpreventable.
In short, something like this where a single individual is able to compromise Twitter and tweet from many different accounts is unlikely as this will likely now be safeguarded against via better employee training in cyber security and two-factor authentication. However, Twitter being attacked again and access being gained is less of a question of if they will be hacked but when they will be hacked next.
If you have any suggestions or improvements for the blog then please send them to [email protected].
25th July 2020
Comments 0
Comments are currently disabled but will be implemented soon.