
Cyber: Social Engineering 101
Cyber Security is a massive field with hundreds of different elements that help to create the over-arching ideology. One of the largest and least technical within cyber, is social engineering.
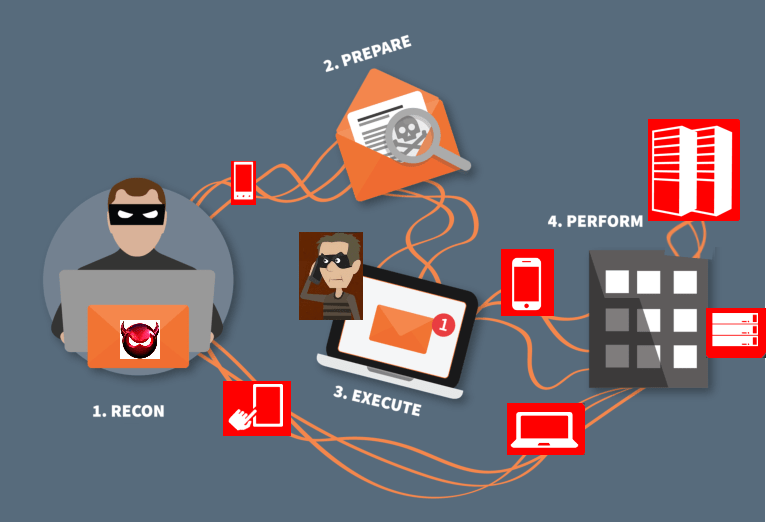
Social engineering is well-known within cyber as a technique mainly used to help gain access to a system using an employee's credentials or existing access, reducing the need to brute-force and guess passwords or keys. The end goal of social engineering is always the same, to gain unauthorized access to a system. Almost all attacks make use of some form of social engineering such as spam emails offering free services or someone trying to catfish you on social media, it can be found everywhere. However, while social engineering can be extremely dangerous, you can learn how to mitigate the risks even without a technical background. Hopefully, this and future posts will help with that.
Before getting into different types of social engineering, I want to firstly say that at some point in time, you will more than likely fall for one of these attacks, whether because you were uneducated before or you simply missed a small element, it's bound to happen and it's important to understand that it isn't your fault. If you work for a company and that company is exposed due to you being targeted, then you can't blame yourself. It's the companies' job to help you understand risks and have measures in place to prevent this from occurring as even professional security experts may fall for this from time to time. I myself have personally experienced one of these types of social engineering and while it did no damage to my financially or any of my data, it still was a wake-up call of how much must be considered at any one time.
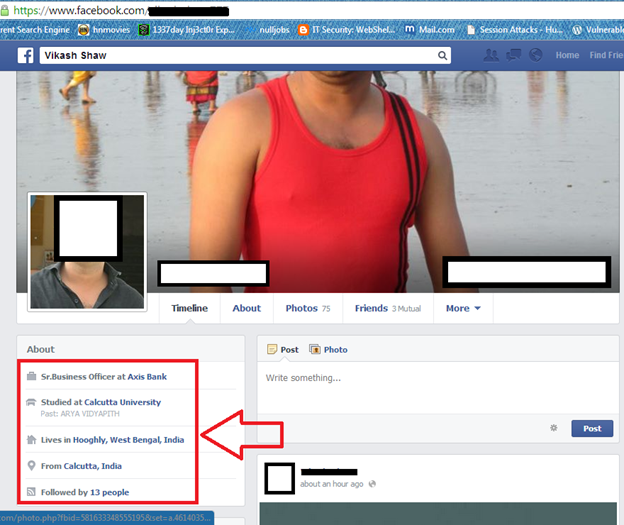
Now the interesting stuff. First, I want to talk about data extraction, the art of retrieving data. The most common source of information right now is social media, without a doubt. There are such large quantities of data being produced at any one time that there is always something new. When Facebook first started, there was a lot less data, but also less privacy. Most people didn't have private accounts that only their friends could see or not show their birthdays, etc. Nowadays, most people don't have their account information filled such as their birthday, so people don't know how old they are. But that's not the only way to get your birthday. Have a look at your timeline, for instance, Facebook. Have a look to see if friends can see it and if anyone has posted on your timeline that it's your birthday. Or maybe, have a look at a family member or friend's profile that you know isn't as private and see if they've posted about you celebrating your birthday. Let's say in one of the posts is a photo with a card in the background saying "Happy 24th Birthday!". From a single photo on someone else's account, you could then find out the exact birthday of someone else.
This many seem scary to think about, but realistically you have nothing to worry about as it's just your date of birth. But if people can gain that information, what else could they get? Maybe your pet's name that you adore, your children's name, a specific place you love to visit or anything else. None of this is an issue unless you use it in your passwords. Be honest, think about all your passwords you have and think about how many of them contain information that relates to you, by that I mean specific words or numbers that relate to you. Now think if you worked at some company that is being targeted and you were singled out as 'vulnerable' due to the amount of information on your profile and possible lack of technical knowledge. They may choose to investigate your profiles in order to examine if they can create passwords from your own data. And if you use those passwords, then theoretically they can gain complete access to your accounts.
Worse to think about is that maybe you don't use any of these details within your passwords, but maybe some of this relates to security questions you setup, similar to a bank that might help an attacker gain access.
But there is a simple solution to all of this. Don't use any personal information in your passwords ever. This is the simplest way to stay safer online. If your passwords don't relate to you then they can't be figured out by an attacker. But you may ask how do I come up with new passwords all the time or even remember them? I don't. I use a password manager myself as I could never remember them all, but I only store some passwords within it. The ones I keep in my head I create by combing words together. For example, look around you and pick 2-4 items and add those next to one another. Maybe substitute a number into the password and you now have a new password that's fairly strong. I'll be releasing a guide to creating passwords soon so check it out here if you want a greater understanding of why they are safer.
But also, before you post something online, possibly think about who it might affect. I'm not saying to never post a single thing ever again and lock your account and never use it, but before you post something, think about if it's an embarrassing picture of your friend or something with some specific information in that might affect them in the future.
As long as you attempt to disassociate yourself from your passwords, you'll be far safer than a lot of other people.
If you have any suggestions or improvements for the blog then please send them to [email protected].
14th August 2020
Comments 0
Comments are currently disabled but will be implemented soon.